Rainbow Six Siege went offline on 27 December 2025 when hackers breached Ubisoft’s backend systems and injected 2 billion R6 credits into player accounts. Servers across PC, PlayStation and Xbox remained down for 48 hours.
Table of Contents
Players Woke to Billions in Premium Currency
Saturday morning, credit balances jumped to billions across all accounts.
Reddit and Twitter filled with screenshots showing 2 billion R6 credits and matching Renown amounts. At Ubisoft’s £79.99 per 15,000 credits, each account held £10.67 million worth of premium currency.
Credits were just the start:
- Ultra-rare “Glacier” weapon skins appeared in inventories
- Developer-only cosmetics unlocked
- Random accounts were banned
- Strange messages replaced ban notifications
Hackers Hijacked the Ban Feed
Instead of security notifications, the ban ticker displayed messages like “What else are they hiding from us?” and “All work and no play makes me a dull boy.”
Lyrics to Shaggy’s 2000 hit “It Wasn’t Me” also scrolled across screens.
“Everyone that logs in gets 2 Billion R6 credits, Renown, Developer Skins and Glaciers,” one Reddit user posted. Another wrote: “I just redownloaded this shitty game and of course it is offline because this company can’t fix its hacker issues.”
Ubisoft confirmed the breach at 9:10 AM EST through the official Siege X account. “We’re aware of an incident currently affecting Rainbow Six Siege. Our teams are working on a resolution.”
Less than two hours later, Ubisoft took all servers offline.
How the Attack Worked
Early reports blamed CVE-2025-14847, a MongoDB vulnerability called “MongoBleed.” Security researchers at BleepingComputer later confirmed hackers exploited authentication flaws in R6 Siege’s backend APIs instead. These APIs are communication channels between different parts of the game, like the link connecting what players see to the database storing their items and currency.
Attackers accessed administrative tools controlling inventories, currency and ban systems. Backend services accepted commands without verifying senders. The 2 billion credit injections bypassed transaction limits. Anomaly detection systems didn’t trigger.
Hackers manipulated ban feeds, distributed premium items and altered account statuses.
Emergency Shutdown and Rollback
On 28 December, Ubisoft announced plans to roll back all transactions after 10:49 UTC on 27 December.
“Nobody will be banned for spending credits received,” the official account posted. Players who bought items with hacked credits avoided punishment through the rollback, which erased those purchases.
Testing took over 24 hours before services resumed. Hacked purchases disappeared while legitimate transactions from before 10:49 UTC on 27 December stayed on accounts.
Servers Reopened, Marketplace Still Down
The tactical shooter came back online on 29 December with inventories restored to pre-breach states for most accounts.
Some inventory glitches persisted. Anyone who connected between 27-29 December temporarily lost access to owned items. Ubisoft said on 29 December that corrections would finish within two weeks.
Ubisoft kept the Marketplace offline pending investigation results.
Steam concurrent player numbers returned to normal around 50,000 to 60,000.
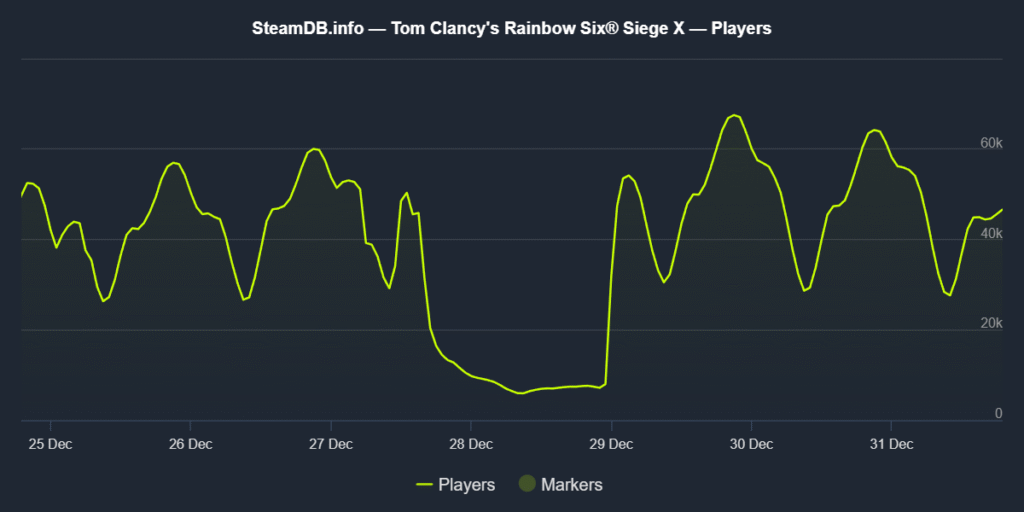
Competitive Players Lost Practice Time
The holiday break timing made the 48-hour outage disruptive for competitive players. Professional teams in North America and Europe cancelled scrimmages and practice sessions. IGN reported esports organisations criticised the timing ahead of upcoming tournaments.
“I see. So they can roll back transactions when it conveniences them, but if we are the ones that get f***ed over, there’s nothing they can do,” one Reddit user wrote.
Another posted: “This sucks. Some people spend a lot of money on this.”
Ubisoft’s 2013 Security Breach
In 2013, Ubisoft experienced a breach that compromised usernames, email addresses and encrypted passwords for 58 million accounts. Password resets followed.
This breach targeted different systems. Ubisoft says no personal data, passwords or payment information leaked. Hackers went after game service APIs rather than customer databases.
Siege launched in 2015 and accumulated complex backend infrastructure over ten years of operation.
What Players Can Do
Servers now operate normally. Anyone who avoided logging in during the breach saw no account changes.
Ubisoft hasn’t required password resets. Security-conscious players can:
- Check login history through Ubisoft Connect
- Turn on two-factor authentication
- Watch for unusual account activity
Competitive players should verify their rank, stats and loadouts before jumping into ranked matches.
The Marketplace remains closed with no reopening date. Ubisoft has not yet explained how hackers gained administrative access to its systems.


